
The .NET Stacks #42: 🔌 When Active Directory isn't so active
This week, we discuss the Azure AD outage and also talk about a variety of other topics.
Happy Monday to you all. Here’s what we have on tap this week.
- One big thing: When Active Directory isn’t so active
- The little things: A bunch of odds and ends
- Last week in the .NET world
One big thing: When Active Directory isn’t so active
Mondays are typically long days. Tell that to Microsoft, who last Monday suffered another Azure Active Directory outage that took down most apps consuming AD, including the Azure Portal, Teams, Exchange, Azure Key Vault, Azure Storage, and more. The outage lasted a few hours (2 pm until 7 pm, in these parts), but lingering effects lasted much longer. The timing was unfortunate—isn’t it always?—as they’re rolling out 99.99% availability in April to customers with Premium licenses.
What happened? Azure AD runs an automated system that removes keys no longer in use. To support a “complex cross-cloud migration,” a specific key was marked to retain for longer than usual. Due to a bug, the system ignored the flag, the key was removed, and Azure AD stopped trusting the tokens from the removed key. When you pair this with the outage from September 2020—the culprit there was a code defect—you have a right to be concerned about Azure AD if you aren’t already.
Meanwhile, updates were quicker on Twitter than on their status pages. Microsoft has owned up to this, saying: “We identified some differences in detail and timing across Azure, Microsoft 365 and Dynamics 365 which caused confusion for customers … We have a repair item to provide greater consistency and transparency across our services.”
For Microsoft’s part, the notice says they are engaged in a two-stage process to improve Azure AD, including an effort to avoid what happened last Monday. This effort includes instituting a backend Safe Deployment Process (SDP) system to prevent these types of problems. The first stage is complete, and the second stage is planned for completion later this year.
Let’s hope so. It’s hard to swallow that such a critical service has a single point of failure. While there are many reasons for and against this design, we can all agree that Microsoft needs to improve resiliency for Azure AD. Instead of the time-honored tradition of Azure executives at Build or Ignite showing off a global map of all their new regions, I think we’d much rather have a slide showing off improvements to their flagship identity service.
The little things: A bunch of odds and ends
In the ASP.NET standup this week, James Newton-King joined Jon Galloway to talk about gRPC improvements for .NET 5. It gets low-level at times, but I enjoyed it and learned a lot.
For the improvements, benchmarks show the .NET gRPC implementation just behind Rust (which isn’t a framework, so that’s saying something). Server performance is 60% faster than .NET Core 3.1, and client performance is 230% faster.
To answer your next question: since IIS and HTTP.sys now support gRPC, does Azure App Service support it too? Not yet, but keep an eye on this issue for the latest updates.
Adam Sitnik, an engineer on the .NET team and the person behind BenchmarkDotNet, has a new repository full of valuable resources for learning about .NET performance.
Steve Sanderson, the creator of Blazor (and a recent interview subject), has created an excruciatingly detailed Blazor issue in GitHub to catch and handle exceptions thrown within a particular UI subtree. This capability accomplishes an idea of “global exception handling” in Blazor.
This week, Nick Craver noted why Stack Overflow likely isn’t migrating to .NET 5. (You’ll want to read the entire thread for context.)
I got several pings about .NET 5 for Stack Overflow over break: unfortunately, no good news there.
— Nick Craver (@Nick_Craver) March 16, 2021
We've hit many flaky build failures with the .NET 5 SDK even when building 3.1, so many that we've reverted back to the 3.1 SDK and have no timeline on a 5.x rollout.
Shay Rojansky notes that EF Core is now fully annotated for C# reference nullability. As a whole, fully annotating nullability across .NET should be complete in .NET 6.
I’ve been intrigued this week by Daniel Terhorst-North writing about why he feels “every single element of SOLID is wrong.” It’s quite the statement, but the more you read, the less revolutionary it sounds. Things change and evolve. Whether it’s SOLID or any other prescribed “best practice,” I’ve learned to take things with a grain of salt and consider the tradeoffs.
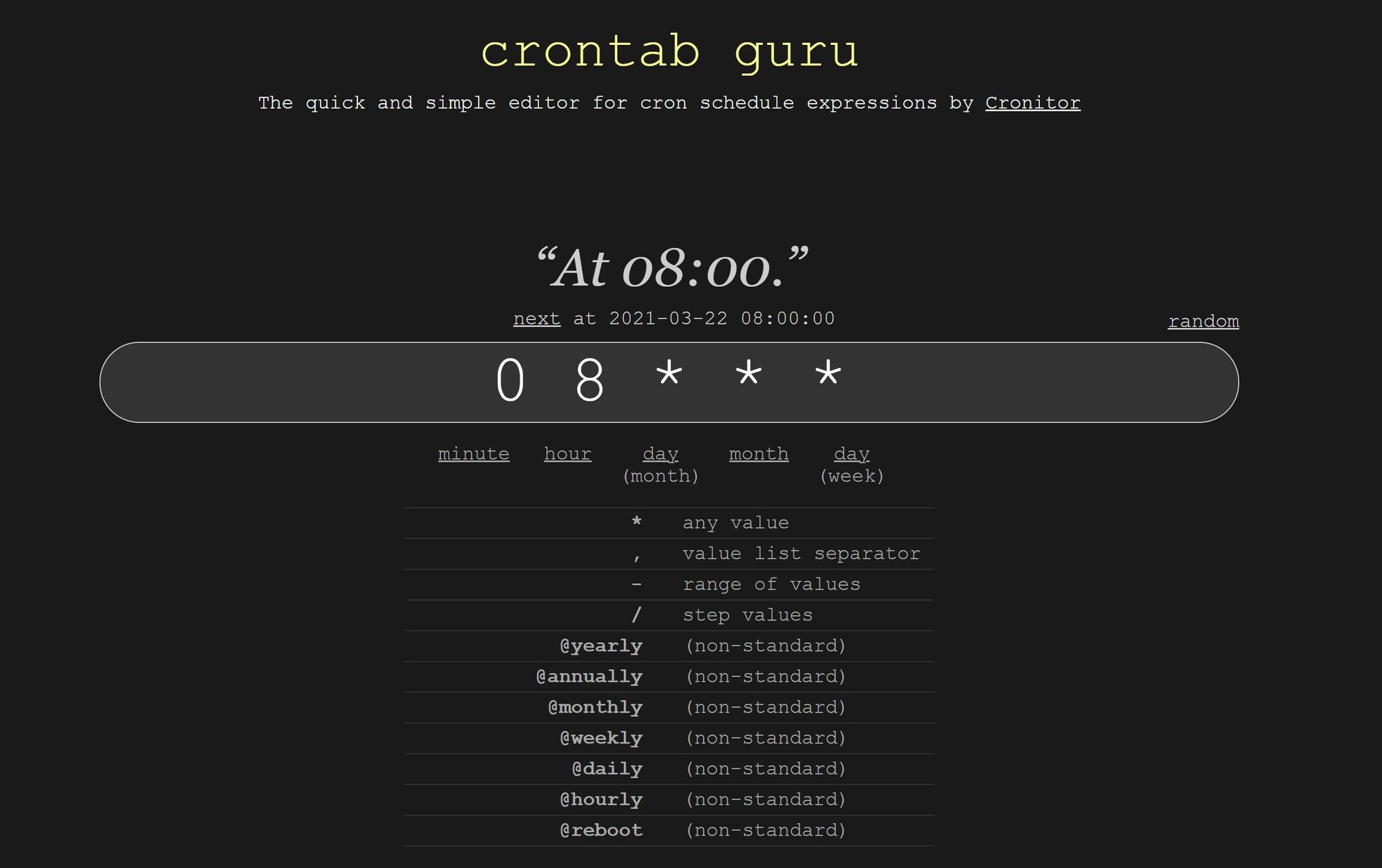
I’ve been working with many scheduled GitHub Actions to automate much of how I put together this newsletter every week (like adding links to a persistent store and generating my Markdown file). With scheduling tasks, as in timed Azure Functions triggers, CRON is still king. It’s nice that GitHub Actions translates CRON syntax for you on hover, but I’m still going to mess it up.
What saves me every time is the crontab.guru site. (I’m not being asked to say this. I’m just a fan.) You can edit a CRON expression and easily see how it looks for a CRON amateur. You can also hit quick links with examples ready to go, like crontab.guru/every-day-8am.
🌎 Last week in the .NET world
🔥 The Top 4
- Thomas Ardal avoids password reuse with Pwned Passwords and ASP.NET Core.
- Jon Gallant writes how the Azure SDK team decided to capitalize the T in Azure.IoT.
- Andrew Lock runs Kubernetes and the dashboard with Docker Desktop.
- Niels Swimberghe creates ZIP files on HTTP request without intermediate files using ASP.NET MVC, Razor Pages, and endpoints.
📢 Announcements
- Sourabh Shirhatti writes how OpenTelemetry has reached v1.0.
- Michael A. Hawker announces Windows Community Toolkit v7.0.
- Bri Achtman provides ML.NET and Model Builder March updates.
- Norm Johanson and Philip Pittle writes about the new deployment experience for AWS on .NET.
- Jon Douglas writes about the NuGet 5.9 release.
- Antonin Prochazka announces PostSharp 6.9 RC.
- JetBrains releases Rider 2020.3.4 and ReSharper 2020.3.4, and also brings scaffolding for ASP.NET Core projects Rider 2021.1.
- Visual Studio 2019 v16.9.2 is now available.
- Taylor Blau recaps Git 2.31.
📅 Community and events
- For community standups: Machine Learning talks about extending ML.NET and ASP.NET talks to James Newton-King about recent gRPC performance improvements.
- Nick Randolph writes about a vision for the Windows developer platform and also wants to stop talking about UWP.
- David Ramel writes how the Windows Community Toolkit is getting the .NET Standard MVVM Library, and also writes about the slow EF Core adoption.
- Dirkjan Bussink writes about how GitHub found and fixed a rare race condition in its session handling.
- The .NET Docs Show talks to Vahid Farahmandian about the Middle East’s largest maritime ERP.
🌎 Web development
- Dave Brock adds a shared dialog component in Blazor.
- Josef Ottosson selects an action method based on header values in ASP.NET Core.
- David Grace writes about how to read the appsettings.json Configuration File in ASP.NET Core.
- Scott Brady integrates ASP.NET identity password policies with password managers.
- Ian Russell works with F# and Giraffe.
- Muhammed Saleem uses Azure SQL with an ASP.NET Core Web API.
- Khalid Abuhakmeh resolves services in ASP.NET Core.
- Isaac Levin writes about migrating the Rock, Paper, Scissors, Lizard, Spock (RPSLS) site to .NET 5 and Blazor Web Assembly.
⛅ The cloud
- Aaron Powell continues his series on GraphQL on Azure with some SignalR.
- Mark Heath generates an Azure Blob Storage User Delegation SAS.
📔 Languages
- Matthew MacDonald writes about three possible C# 10 features.
- Dave Brock uses C# to upload files to a GitHub repository.
- Khalid Abuhakmeh creates a Zip file with .NET 5.
🔧 Tools
- Laurent Kempé works on service-to-service invocation with the Dapr SDK.
- Donovan Brown develops Dapr components in a container.
- Scott Hanselman writes about Ryujinx, an experimental Nintendo Switch emulator written in C# for .NET Core.
- Khalid Abuhakmeh generates Dockerfiles for .NET applications with Rider.
- David Ramel writes about WinUI teaming up with Uno for cross-platform apps.
📱 Xamarin
- Brad Dean updates a Xamarin.Forms project to MAUI.
- Jesse Liberty writes about Xamarin best practices.
- Leomaris Reyes works with local notifications in Xamarin.Forms.
- James Montemagno builds settings screens for Xamarin.Forms.
🏗 Design, testing, and best practices
- Steve Smith writes about how hardware hides many sins.
- Derek Comartin decomposes CRUD to a task-based UI.
- Richard Lander investigates a Linux CVE with .NET images.
- Daniel Terhorst-North writes about his distaste for SOLID.
- Ian Miell asks: when should I interrupt someone?
- Jason Farrell addresses the misconception that Entity Framework needs a data layer.
- Jon Hilton builds design system–friendly components.
- Subodh Sohoni writes about microservices.
- Mark Seemann writes about using pure functions by default.
- Amy Rigby writes how consistency can make you successful.
- Damien Bowden writes about the authentication pyramid.
🎤 Podcasts
- The Complete Developer podcast talks about coding coding analyzers.
- The 6-Figure Developer podcast has agile conversations with Fredrick & Squirrel.
- The Azure DevOps Podcast talks to Richard Campbell on the Humanitarian Toolbox.
- The .NET Rocks podcast talks about MongoDB in the cloud.
- RunAsRadio talks to Anna Hoffman about migrating to Azure SQL.
🎥 Videos
- James Montemagno works on HTTP web requests with data caching.
- The ON .NET Show discussing messaging patterns for .NET developers.
- The ASP.NET Monsters discuss output formatters in ASP.NET Core.
- Data Exposed recaps what’s new in Azure SQL auditing.





