
The .NET Stacks #20: Route to Code, IdentityServer, community links
This week, we look at Route to Code and check in on big IdentityServer news.
Based on my eating habits this week, I should probably rename this newsletter to The .NET Snacks.
This week:
- Use “route to code” with ASP.NET Core
- The IdentityServer project goes commercial
- Understand Blazor Web Assembly performance best practices
- Last week in the .NET world
Use “route to code” with ASP.NET Core
I’ve been thinking a lot about “route to code” in ASP.NET Core lately. There isn’t much out there but have found some good content: the ON.NET Show brought up the concept recently, and Anthony Giretti has been writing some nice posts about it lately, too.
As an ASP.NET developer, you’ve likely leveraged controllers in MVC or Web API apps. That is, the controller will intercept your HTTP request and handle routing for you—you can do some configuration, but it’s largely managed for you. This is great if you don’t need much control, but it sure adds a lot of ceremony (if you’ve ever wait for ASP.NET to scaffold a new MVC app, you know what I mean). You may have scenarios where you need fine-grained control, simplicity, or high performance without an explicit framework.
This “route to code” concept offers a solution somewhere between ASP.NET Core middleware and controllers—where you can handle routing right in the Startup.cs file of your ASP.NET Core project. You can get started by creating an “Empty” ASP.NET Core web app in Visual Studio.
If we look at Anthony’s example, he creates a list of countries and instantiates it in the Startup constructor. The fun stuff, though, is in the app.UseEndpoints middleware.
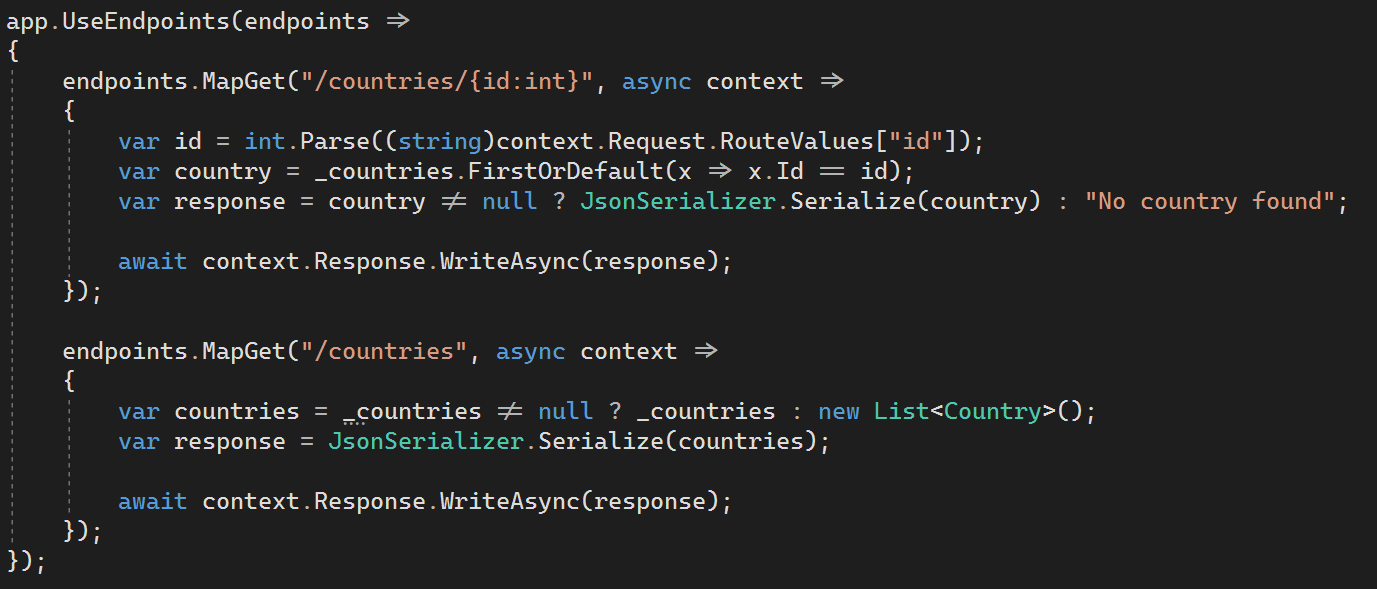
Here, we’re using the MapGet extension method—you use it to match the HTTP/URL method, and then execute by running a delegate (and yes, there are other methods for the other HTTP verbs). You can definitely use this in more complex ways—like using string interpolation to create routing templates, adding authentication, and dependency injection. It takes some getting used to after years of depending on controllers—but it’s a great way to cut straight to what matters.
The IdentityServer project goes commercial
This week, it was announced that IdentityServer—an open-source OpenID Connect (OIDC) and OAuth 2.0 framework for ASP.NET and ASP.NET Core—has gone commercial. With 12 million NuGet downloads to date for the IdentityServer4 package, this is a big deal. For most of us, we’ve used the free (for us) library for the last decade. While congratulations are in order for Brock Allen and Dominick Baier—and they should be praised for finding a path for sustaining the project over the long term—a logical next question is what this means for the greater .NET ecosystem.
From Dominick Baier’s post on the news:
The current version (IdentityServer4 v4.x) will be the last version we work on as free open source. We will keep supporting IdentityServer4 until the end of life of .NET Core 3.1 in November 2022.
To continue our work, we have formed a new company Duende Software, and IdentityServer4 will be rebranded as Duende IdentityServer. Duende IdentityServer will contain all new feature work and will target .NET Core 3.1 and .NET 5 (and all versions beyond).
What does this mean for use in your projects? IdentityServer4 is still free, and appears to always will be. However, in two years it won’t be supported and you won’t get any critical security updates for it. IdentityServer5 will have this new pricing model. (And short term, .NET will ship with IdentityServer 4 templates.)
As for that pricing model: this new Duende IdentityServer company will offer two versions of IdentityServer. You’ll have a free reciprocal public license (RPL) for folks using open-source work, and a commercial license that is paid (the exact charges based on company size and usage). I’m seeing the $1500 price point being passed around, but others have noted it isn’t so simple. You’ll also want to check out the lively GitHub issue that discusses where to go from here.
If you don’t want to pay for it, fine—you’ve got two years on IdentityServer4 and you can evaluate if less complex solutions like the out-of-the-box Microsoft.AspNetCore.Identity work better for you. If not, you can roll your own solution. To that I say: unless you’re a security expert you’ll probably find the cost in development time and headaches far exceeds licensing for IdentityServer (for most cases). If your company needs the complex use cases and can pay for it, my opinion is to do just that.
Understand Blazor Web Assembly performance best practices
This week, Steve Sanderson—the architect at Microsoft behind Blazor—announced he’s working on documenting Blazor Web Assembly performance best practices. While performance is always important, it appears doubly so when you’re loading a complete .NET runtime into the browser. I definitely learned a lot, and it’s worth a read.
🌎 Last week in the .NET world
🔥 The Top 3
- Heather Downing talks about building securely with Blazor Web Assembly.
- Patrick Smacchia discusses app trimming in .NET 5.
- Phil Haack finds a subtle gotcha with Azure deployment slots and ASP.NET Core.
📢 Announcements
- Microsoft released its survey results on repo experience, and folks in the WPF community have voiced their displeasure.
- Maria Naggaga announces .NET Interactive Preview 3.
- Bri Achtman gives us September updates on ML.NET.
- David Ortinau previews Xamarin.Forms 5’s advanced UI controls.
📅 Community and events
- The .NET Docs Show double-clicks on accessibility and autonomous systems with John Alexander.
- JetBrains has some nice .NET OSS ideas for Hacktoberfest.
- Three .NET community standups this week: Xamarin talks with Theodora Tataru, Entity Framework runs through geographic data with NetTopologySuite, and ASP.NET runs through .NET 5 with Scott Hunter.
😎 ASP.NET Core / Blazor
- Shaun Curtis adds new record types to his Blazor database app.
- Jon Hilton renders diagrams on the fly in Blazor, and also discusses when Blazor decides to render your UI.
- Michael Shpilt uses attributes and middleware in ASP.NET Core.
- Michał Białecki reads request headers as an object in ASP.NET Core.
- Anthony Giretti uses Microsoft.AspNetCore.Http JSON extensions to assist with “route to code.”
- Andrew Lock sets environment variables for ASP.NET Core apps in a Helm chart.
⛅ The cloud
- Pavel Krymets discusses connection pool limits for .NET Framework when using the new .NET Azure SDK.
- Muhammed Saleem publishes an ASP.NET Core app to Azure App Service from Visual Studio.
📔 C#
- Khalid Abuhakmeh reads and converts QueryCollection values in ASP.NET.
- Franco Tiveron shows how to use SameSite with .NET.
- Matthew Jones discusses casting, conversion, and parsing in C#.
- Khalid Abuhakmeh serializes interface instances with System.Text.Json.
- David Grace shows off four new C# 9 features.
- Matthew Jones runs through primitive types, literals, and nullables in C#.
- Konrad Kokosa explores getting rid of array bound checks, ref-returns, and .NET 5.
- Mark Seemann uses EnsureSuccessStatusCode as an assertion.
📗 F#
- A nice piece on how to use JWT with RSA in F#.
- Bartosz Sypytkowski works on CRDTs with arrays in F#.
- Wojciech Gawroński tries out F# with AWS.
- Ryan Palmer works with the Fabulous project with Xamarin and F#.
- Jeremie Chassaing works with applicatives.
🔧 Tools
- Dominick Baier writes about the future of IdentityServer.
- Michał Białecki talks about how not to pass parameters in Entity Framework 5.
- Kevin Logan writes about transitioning from TFVC to Git.
- Nicholas Blumhardt works with user-defined functions in Serilog expressions, and also discusses programmable text and JSON formatting for Serilog.
- Scott Hanselman works with dotnet-monitor.
- The Edge team talks about bringing the browser dev tools experience to Visual Studio Code.
- Sophia Prafina writes about avoiding Kubernetes anti-patterns.
- Dmitrij Kovaliov writes about resiliency in your .NET apps with Polly.
- Ian Griffiths minimizes allocations in AIS.NET.
- Dan Clarke shows how to deal with unrelated changes on feature branches with Git.
- James Dawson streamlines .NET dependency management with NuGet meta packages.
- David Walsh shows how to detect the default branch in a Git repository.
- Neils Swimberghe writes a PowerShell script to scan documentation for broken links.
📱 Xamarin
- Jean-Marie Alfonsi hunts down Xamarin shadows leaks on Android.
- Denys Fiediaiev creates a custom Xamarin pop-up using MvvmCross.
- Leomaris Reyes replicates a Sneaker UI app.
- Alex Shirshov shows you to use C# 9 in Xamarin today.
🎤 Podcasts
- Scott Hanselman talks to Dr. Michaela Greiler about enjoyable code reviews.
- The Microsoft Cloud Show recaps Ignite 2020.
- The Coding Blocks podcast continues looking at the DevOps Handbook.
- The 6-Figure Developer podcast talks about MLOps and ML.NET with Alexander Slotte.
🎥 Videos
- The IoT Show talks about connecting sensors to Azure.
- The Visual Studio Toolbox talks about the Bridge to Kubernetes feature.
- The AI Show automates machine learning on Azure.
- Azure Friday goes under the hood with Azure Container Instances (ACI).
- The ASP.NET Monsters discusses static site generators with Khalid Abuhakmeh.
- Data Exposed begins a series on Infrastructure as Code and Azure.





